What CIS Controls Should a Small Professional Services Firm Actually Implement?
Small professional services firms don’t need hundreds of cybersecurity tools—but they do need the right foundational controls. For firms with 25–75 employees, the CIS Critical Security Controls provide a practical, prioritized framework for reducing cyber risk without enterprise-level complexity.
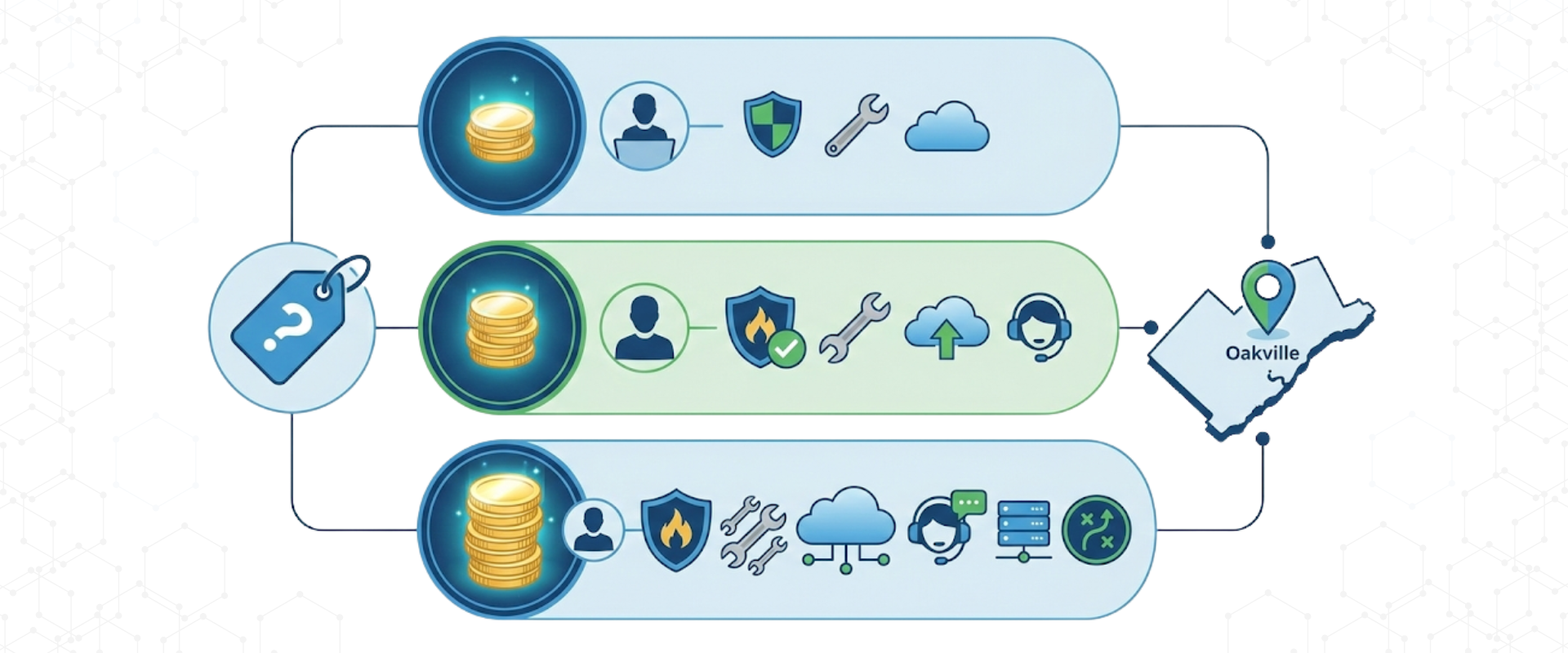
In the Oakville and GTA West market, firms investing $200–$250 per user per month in managed IT services should expect their MSP to implement the first 8–10 CIS controls as part of a standard, security-first offering. These controls form the baseline for protecting client data, meeting cyber-insurance requirements, and reducing the likelihood of ransomware and data breaches.
Below is a practical breakdown of the CIS controls that actually matter for small professional services firms—and how they should be implemented in the real world.
What Are the CIS Critical Security Controls
(in Plain Language)?
The CIS Critical Security Controls are a set of 18 prioritized security safeguards developed by cybersecurity experts worldwide. They are designed to help organizations:
- Focus on what matters most
- Reduce common attack paths
- Improve security maturity over time
For small and mid-sized firms, the goal is not to implement all 18 controls at once. The goal is to start with the most impactful controls and build from there.
The 8 CIS Controls Every Small Professional Services Firm Should Start With
1. Inventory and Control of Enterprise Assets (CIS Control 1)
You can’t protect what you don’t know exists.
At a minimum, firms should have:
- A complete inventory of laptops, desktops, servers, and network devices
- Visibility into which devices are active or inactive
- Alerts when new or unauthorized devices appear
Many security failures begin with unknown or unmanaged devices. Asset visibility is the foundation of everything else.
2. Inventory and Control of Software Assets (CIS Control 2)
Unapproved or outdated software creates risk.
This control ensures:
- Approved software lists are defined
- Unauthorized applications are identified and removed
- Vulnerable or outdated software is patched or eliminated
For professional services firms, this reduces exposure from shadow IT, legacy applications, and unpatched tools.
3. Data Protection (CIS Control 3)
Client data is often your most valuable asset—and your biggest liability.
This control focuses on:
- Knowing where sensitive data lives
- Ensuring data is encrypted where appropriate
- Limiting access to only those who need it
- Protecting data in backups and cloud platforms
Firms that handle legal, financial, or architectural data are especially exposed if data controls are weak or undocumented.
4. Secure Configuration of Enterprise Assets and Software (CIS Control 4)
Many breaches occur not because systems are missing—but because they are misconfigured.
This control includes:
- Secure baseline configurations for devices and servers
- Removal of unnecessary services and features
- Ongoing configuration management
Standardized, hardened configurations significantly reduce attack surfaces and repeat issues.
5. Account Management and Access Control (CIS Controls 5 & 6)
Identity is now the primary attack vector.
Firms should expect:
- Centralized user account management
- Role-based access (users only have what they need)
- Multi-factor authentication (MFA) for email, cloud apps, VPNs, and admin access
- Regular access reviews
Credential theft remains one of the most common causes of breaches. Strong identity controls dramatically reduce that risk.
6. Continuous Vulnerability Management (CIS Control 7)
Unpatched systems are easy targets.
This control ensures:
- Systems are scanned for vulnerabilities
- Patches are applied regularly
- High-risk issues are prioritized and tracked
Professional services firms often delay updates due to fear of disruption—but unmanaged vulnerabilities create far greater risk.
7. Audit Log Management (CIS Control 8)
When something goes wrong, logs tell the story.
This control focuses on:
- Centralized logging from endpoints, firewalls, and cloud systems
- Retention of logs for investigation and compliance
- Reviewing logs for suspicious activity
Without logs, firms are blind to what happened—and insurers and auditors will notice.
8. Malware Defenses and Monitoring (CIS Controls 10 & 13)
Modern threats require more than basic antivirus.
Firms should expect:
- Managed endpoint protection and EDR
- Behavioral detection (not just signature-based)
- Continuous monitoring and alerting
- Human oversight, not just dashboards
This dramatically reduces the likelihood of ransomware spreading undetected.
How CIS Controls Map to Real Business Outcomes
Implementing these controls isn’t about checking boxes—it’s about outcomes:
- Fewer security incidents
- Faster detection and response
- Improved cyber-insurance approvals
- Greater client confidence
- Reduced operational disruption
For leadership, this means fewer emergencies and clearer answers when clients or insurers ask about security.
Real-World Example: CIS Controls in Action
A 30-employee professional services firm had basic antivirus, inconsistent MFA usage, and limited visibility into devices and software.
After their MSP implemented the first set of CIS controls:
- MFA coverage increased from
~40% to 100%
- All devices and software were inventoried and standardized
- Backup reliability exceeded
99.9%
- The firm passed a cyber-insurance renewal with no exclusions
- No successful phishing or ransomware incidents occurred in the following year
Security didn’t become “perfect,” but it became measurable and defensible.
How Many CIS Controls Should a Small Firm Implement?
Most small professional services firms should:
- Start with the
first 8–10 CIS controls
- Implement them
fully and consistently
- Improve maturity over time
Trying to implement everything at once usually leads to partial, poorly managed controls—which is worse than doing fewer controls well.
What Your MSP Should Be Doing for You
If you’re paying $200–$250 per user per month, your MSP should:
- Understand CIS controls deeply
- Implement core controls by default
- Explain them in business terms
- Continuously review and improve them
- Map them to insurance and compliance needs
If CIS controls are unfamiliar or treated as optional, that’s a red flag.
CIS vs. NIST: Do You Need Both?
CIS and NIST are complementary:
- CIS = practical, prioritized safeguards
- NIST = broader governance and risk framework
Most small firms start with CIS and later map progress to NIST as maturity grows.
Trust Signals to Look For in an MSP
When evaluating CIS implementation, look for MSPs that:
- Include CIS controls by default
- Standardize security tools across clients
- Provide regular security reviews
- Track progress and outcomes over time
- Have experience supporting firms like yours
Security isn’t about buying more tools—it’s about building a system that reduces risk consistently.
Frequently Asked Questions
What are the CIS Critical Security Controls?
The CIS Critical Security Controls are a prioritized set of safeguards designed to help organizations reduce the most common cybersecurity risks. They focus on practical, proven actions rather than complex or theoretical security measures.
How many CIS controls does a small firm actually need?
Most small professional services firms should start with the first 8–10 CIS controls. Implementing a smaller number well and consistently is more effective than trying to adopt all controls at once.
Do CIS controls replace the need for cybersecurity tools?
No. CIS controls guide how tools should be selected, configured, and managed. They emphasize process, consistency, and outcomes rather than relying on individual products alone.
Why do insurers and clients care about CIS controls?
CIS controls demonstrate that a firm follows recognized security best practices. Insurers and clients use them as evidence of reduced risk, better preparedness, and more mature security management.